Which of the Following Best Describes Dns
View Review Questions 2docx from SVAD 231 at Ivy Tech Community College Indianapolis. Which of the following netcat commands would he enter on the two computers.

Ssl Certificate For Wordpress On Rackspace Cloud Sites Ssl Certificate Clouds Certificate
A policy that ensures that each employee only has access to the exact data needed to fulfill his or her job and nothing more.

. Choose all that apply a. Firewall to block connection attempts to dynamic DNS hosts. Which Of The Following Best Describes Why We Have Seasons On Earthastronomy midterm 1QuestionAnswerWhich of the following best describes why we have seasons on EarthThe tilt of Earths axis causes different portions of the Earth to receive more or less direct sunlight at different times of yearW.
An attacker taking control of a session between the server and a client. It hosts a primary zone for your public Internet domain name which is different from your internal Active Directory domain names. It allows an attacker to use an already established connection.
Which of the following best describes session hijacking. The government is the driving force in the US. This is a false positive and the scanning plugin needs to be updated by the vendor.
Choose all that apply Hierarchical database. Providing false identity information to gain unauthorized access. Session hijacking subverts the UDP protocol.
A tree is a group of one of more domains all of which share a. Which of the following statements best describes the term resolver. A nameserver that can resolve non-local domains.
In an interview you are asked to configure a DNS server on a Linux machine. This is a true negative and the new computers have the correct version of the software. Which of the following best describes DNS.
On each DNS server except DNS-Int configure a forwarder pointing to DNS-Int. You want one or more of your internal servers to be able to handle DNS queries for your public domain and to serve as a backup for the. Which of the following accurately represents an FQDN.
If this is successful an attacker can use an already established TCP connection. Providing a means of establishing DNS redundancy in a cluster configuration. Which of the following statements best describes the relationship today between government and the economy in the United States.
Which of the following best describes trusted location in MS Office. To resolve the IP address 107514388 into a name a DNS server would locate a domain called 1437510in-addrarpa in the usual manner and read the contents of a resource record named 88 in that domain. On each DNS server except DNS-Int configure a root hint to point to DNS-Int and delete all other root hints.
Which of the following is not one of the elements of DNS. You have a DNS server outside your corporate firewall that s a stand - alone Windows Server 2012 R2 server It hosts a primary zone for your public Internet domain name which is different from your internal Active Directory domain names. Which of the following BEST describes the situation.
Which of the following best describes DNS. Which of the following best describes a tree and a forest. Nc -l -p 2222 managers computer and nc -nv 1921683491 2222 Shawns machine Hugh a security consultant recommended the use of an internal and external DNS.
Session hijacking works by first subverting the DNS process. You have a DNS server outside your corporate firewall thats a stand-alone Windows Server 2012 R2 server. DNS servers are used to map a name to an IP address.
Which of the following best describes DNS poisoning. What best describes DNS. Which of the following best describes one of the primary intended purposes of a DNSOnly server.
A policy stating that personal data can only be collected for a specific legal and legitimate purpose and cannot be used any other way. You want one or more of your internal servers to be able to handle DNS queries for your public domain and to serve as a backup for the primary. A Dynamic Names Server is the computer you connect to when you electronically enter the internet that replies with a.
Configure DNS-Int as a forwarder by enabling forwarded requests in the Forwarders tab of the servers Properties dialog box. Please select all the correct answers. Redirecting traffic by changing the IP record for a specific domain.
Trusted location allows you to run macros-enabled files with no security restrictions. Choose all that apply a. An established connection without specifying a username or password.
Which of the following best describes DNS. Which of the following BEST describes a non-disclosure agreement policy. A tree is a collection of two or more forests that form a noncontiguous DNS namespace.
Session hijacking targets the TCP. The government subsidizes economic interests but otherwise leaves them to operate as they please. 4 points Which of the following accurately represents an FQDN.
The economy is largely self-regulating. Which of the following best describes DNS.

3 Effective Ways To Prevent No Name Papers Life Between Summers Student Centered Learning Activities Student Self Assessment Student Centered Learning
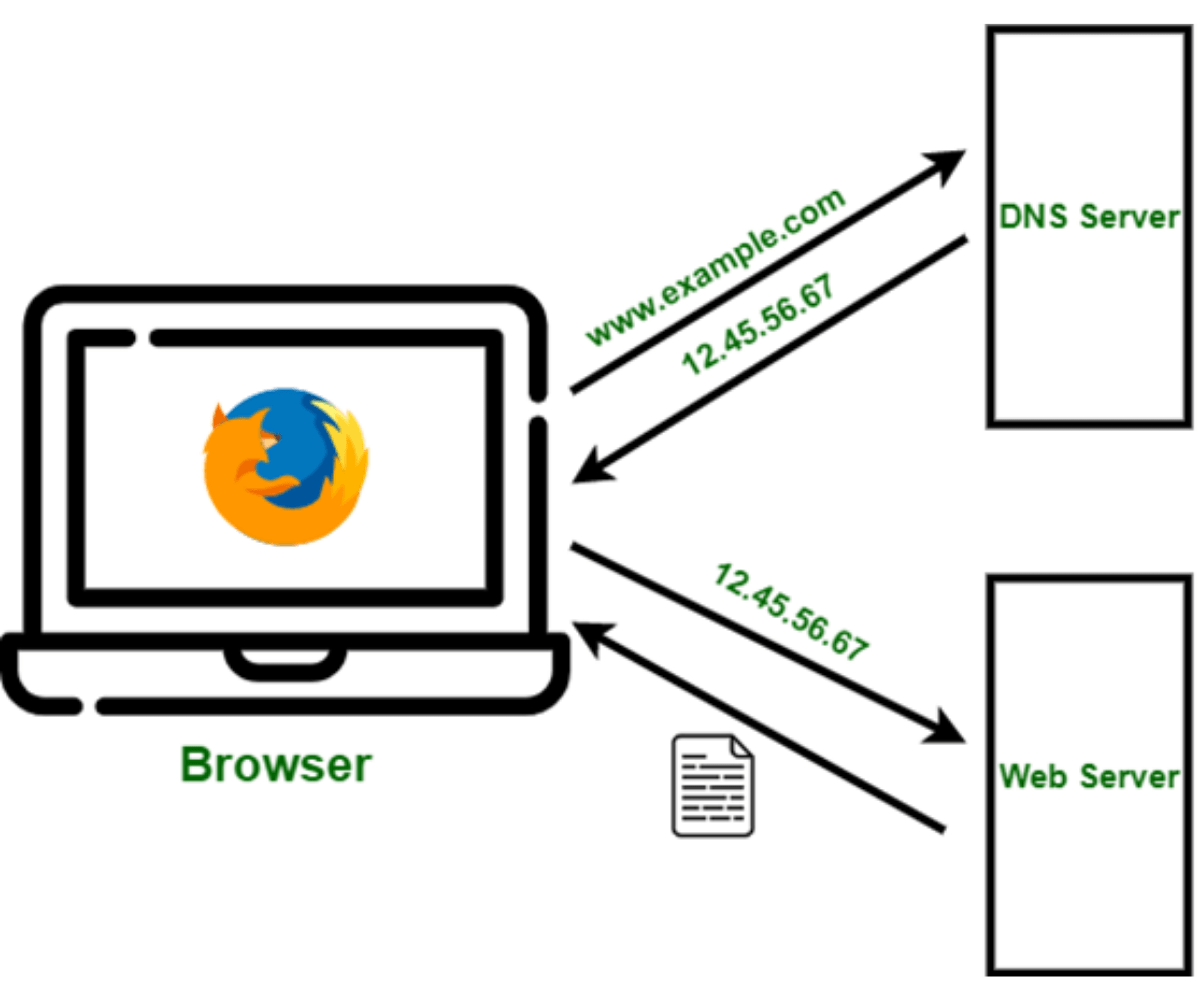
Understanding The Working Of Domain Name System Dns Zindagi Technologies

There Are Many Thinks To Love About Ibvpn That I Consider One Of The Best Vpn Providers It Offers Great Features Ni Great Vegan Recipes Best Vpn How To Plan

Managing Web Host Manager Whm Packages All You Need To Know Web Hosting Business Web Hosting Management

Oscar S 2019 Winners Mind Mapping Software Mapping Software Mind Map

Azure Kubernetes Service Everything You Need To Know Azure Public Cloud Hybrid Cloud

Tcp Ip Vs Osi What S The Difference Between Them Networking Infographic Osi Model Cisco Networking Technology

This Picture Describes How Does The Internet Works In My Opinion This Is A Great Picture Because It Show How Internet Works Local Dating Sites Internet Dating

The One Word That Best Describes Your Day So Far According To Your Zodiac Sign Astrology Signs Zodiac Signs Zodiac Traits

How To Get A Free Ssl Certificate W Let S Encrypt Ssl Certificate Certificate Authority Let It Be

Kate Spade Bandeau Bra Bikini Top Paloma Beach L Bra Bikinis Bikini Tops Bandeau Bra

Dns Dns Lookup Explained Step By Step With Examples Youtube Dns Explained Looking Up

Vpn Error 812 Connection Prevented Because Of Ras Vpn Server How To Find Out Prevention Connection

Linkeddata Semiotic Triangle An Illustration Of The Duality Inherent In Http Uris Re Denotation Naming Via Kide Communication Theory Data Triangle




Comments
Post a Comment